That sinking feeling when you see a strange error on your site, get a warning from Google, or watch your traffic suddenly disappear—it's a moment every website owner dreads. If you’re reading this, you’re probably feeling that exact panic right now. Please, take a deep breath. A hacked website is serious, but it's a problem you can absolutely fix.
Getting a Grip on the Threat
Finding out your WordPress site has been compromised can feel incredibly personal, but it's almost never a targeted attack against you. The reality is, because WordPress powers such a huge chunk of the internet, it’s a constant target for automated bots that do nothing but sniff out small, common vulnerabilities. You’re not alone in this, and you’ve come to the right place for help.
This guide is here to cut through the stress and give you a clear, step-by-step plan for removing malware from your WordPress site for good. We’ll walk through everything together, one step at a time.
Why Do WordPress Sites Get Hacked So Often?
It's a classic double-edged sword: the platform's incredible popularity is its biggest strength and also its most significant weakness. With millions of sites running on WordPress, hackers can simply unleash automated scripts to scan for known weak points on a massive scale.
In the UK, where WordPress is a go-to for countless businesses, it has become an especially juicy target. In fact, an alarming 72.72% of WordPress websites were attacked due to malware, a statistic that really drives home the need for solid security. You can find more WordPress security statistics to see the full picture of the current threat level.
The main thing to realise is that a hack is usually a crime of opportunity, not a personal vendetta. An automated bot simply found a digital window you didn't know was unlocked—often an outdated plugin or a weak password.
What This Guide Will Do for You
Our mission is to replace that feeling of panic with a sense of control. We’re going to cover the entire recovery process, giving you the knowledge to not only clean up your site but to make sure it's much harder for this to happen again.
Here’s a quick look at our game plan:
- Confirming the Hack: First, we'll make sure your site is truly infected and figure out how bad the damage is.
- The Cleanup Plan: Next, we'll lay out the exact steps you need to take to meticulously remove every trace of malicious code and dodgy files.
- Strengthening Your Defences: Finally, we’ll talk about how to build a much stronger security setup to stop this from ever happening again.
Discovering malware is a nightmare, but it doesn't have to be a disaster. With the right know-how and a methodical approach, you can get your site back to full health. Let’s get started.
Confirming a Malware Infection on Your Website

Before you jump into removing malware from your WordPress site, you have to be absolutely sure that's what you're dealing with. It's easy to make things worse or waste hours fixing the wrong problem if you start without a clear diagnosis.
Think of this phase like being a detective at a crime scene. You're looking for clues—any sign of a security breach—to understand how bad the problem is and how to tackle it effectively.
Your Initial Diagnostic Checklist
Let's start with the most obvious signs. These are the classic red flags that usually tell a website owner something is seriously wrong. Run through this list and see if anything looks familiar.
- Unexpected Pop-ups or Redirects: Are visitors complaining about being sent to spammy or malicious websites? This is one of the most common symptoms.
- New, Unfamiliar Admin Accounts: This one's a huge giveaway. Head straight to your WordPress Users list (
yourwebsite.com/wp-admin/users.php). If you spot any administrator accounts you didn't create, you've definitely been compromised. - Performance Drops: Has your site suddenly become painfully slow or unresponsive? Malware often hogs server resources, causing a dramatic slowdown that comes out of nowhere.
- Suspicious Files: Get into your hosting account’s file manager or use an FTP client. Poke around your
wp-content/uploadsdirectory. Look for files with strange names or anything that has been modified recently when you haven't touched the site. - Changes to Your Website: Do you see odd content, links to dodgy pharmaceutical sites, or weird text showing up on your pages, maybe in the header or footer?
If you're nodding along to one or more of these points, it’s highly likely you have an infection. Now, let’s get some more concrete proof.
Using Free Scanners for a Quick Verdict
The good news is you don't need to be a security guru to get a reliable second opinion. There are some excellent free tools out there that can scan your website from the outside, looking for known malware and checking if your site has been blacklisted by search engines.
A great place to start is Sucuri SiteCheck. It’s a free, web-based tool that gives you a quick snapshot of your site's health. Just pop in your domain, and it'll check for common malware, your blacklist status, and other security red flags.
Just remember, these external scanners can only see what a public visitor sees. They can't find malware hidden deep within your server files, but they are incredibly useful for spotting surface-level infections and blacklist warnings.
Another essential tool is Google Search Console. If you have your site verified (and you absolutely should), Google will often alert you to problems in the "Security issues" report. A warning in there is definitive proof that you need to act immediately.
Performing an Internal Scan with a Plugin
For a much more thorough investigation, you need to look inside your WordPress installation. This is where a dedicated security plugin is your best friend. These tools can scan every single file and database table for malicious code, giving you a much clearer picture of the damage.
Wordfence is one of the most popular and effective choices. Once you install it, you can run a full scan that compares your core WordPress files, themes, and plugins against the official versions in the repository. It will immediately flag any modifications, extra files, or known threats.
Here’s what a good internal scanner can find that an external one will almost always miss:
- Modified Core Files: It checks if essential WordPress files have been tampered with to hide malicious code.
- Hidden Backdoors: Hackers love to leave behind "backdoors"—small scripts that give them persistent access to your site. A quality scanner is built to sniff these out.
- Infected Plugin or Theme Files: The scan will pinpoint the exact files within your themes or plugins that have been compromised.
- Database Injections: It can also identify spammy links or malicious scripts that have been injected directly into your site's database, something external tools can't see.
By combining your own observations with the results from both external and internal scans, you can move from suspecting a hack to knowing for sure. This confirmation gives you the solid ground you need before you start the critical work of removing the malware from your WordPress site.
Your Action Plan for WordPress Malware Removal
Alright, you’ve confirmed your site is infected. Now it's time to roll up your sleeves and start the methodical process of cleaning the malware from your WordPress site. This part can feel intimidating, but it's just a series of logical steps. We’ll walk through it together, making sure we don’t miss a thing.
Our goal isn't just to delete a few dodgy files. We need to perform a deep clean, rooting out the infection and any backdoors the attackers have left behind. Think of it like pulling up weeds – you have to get the entire root system, or it’ll just grow back.
The First, Most Critical Step
Before you touch a single file, you absolutely must create a complete backup of your infected website. I know, it sounds completely backwards. Why on earth would you save a copy of a hacked site?
Simple: it’s your safety net.
The malware removal process is delicate work. There’s always a small but real risk you could accidentally delete a crucial file and take your entire site down. This backup is your emergency "undo" button, letting you restore things to their current (albeit infected) state if something goes horribly wrong.
Most hosting providers have a one-click backup tool in their control panel. Use it now. Once that backup is safely stored, you can get to work with peace of mind.
A Layered Approach to Cleaning
Properly removing malware isn't a single action; it’s about attacking the problem from multiple angles. We're going to use a layered strategy to ensure no malicious code gets left behind.
First, let's get a picture of the core process. A typical cleanup involves scanning for threats, identifying what they are, and then systematically cleaning or replacing the files that have been compromised.
This is a simplified look at how you'd scan and clean your site's files.
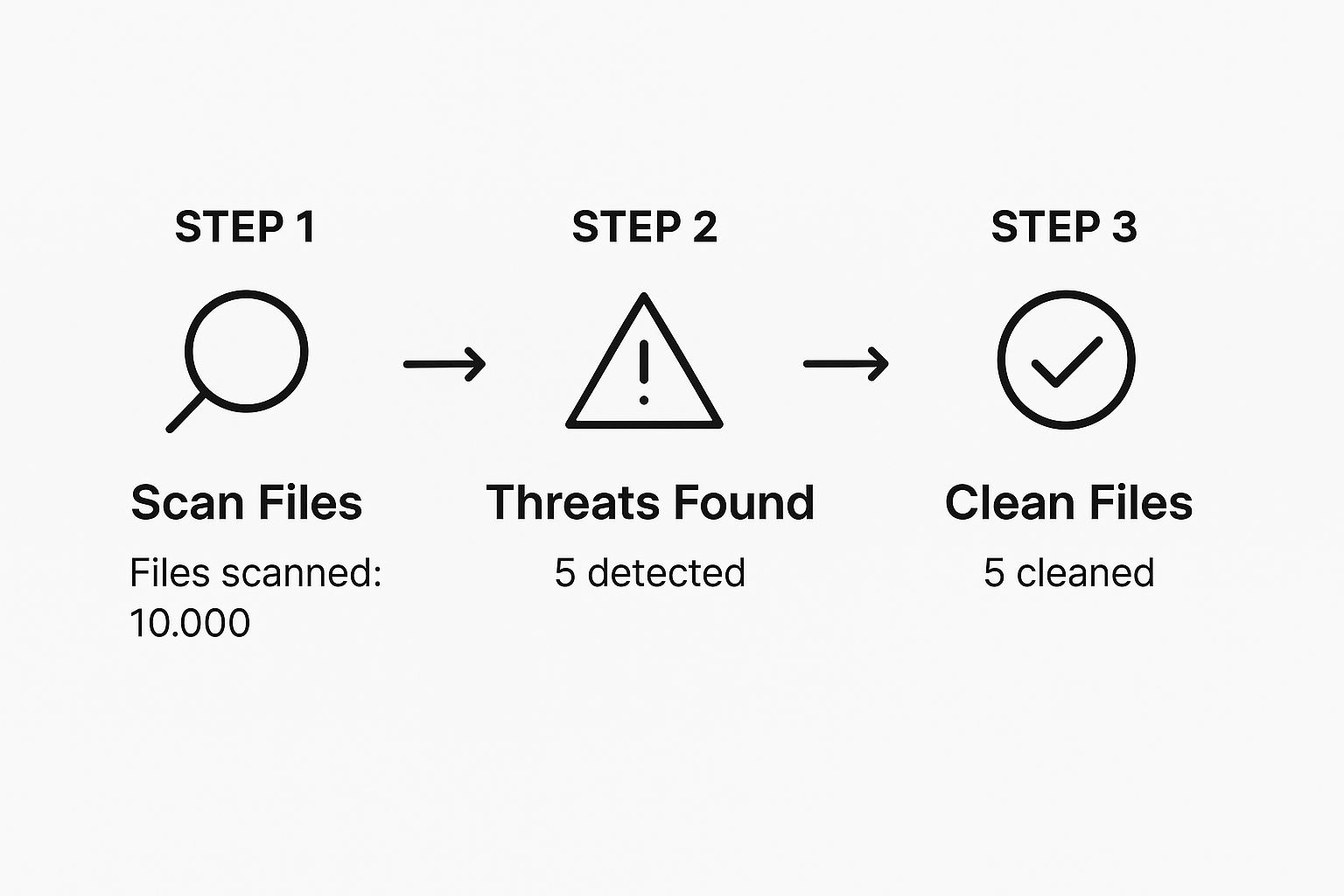
This illustrates that fundamental scan-and-clean loop. It’s the heart of restoring your site’s integrity, making sure every threat we find is dealt with.
Now, let's apply this logic to the specific components of your WordPress installation.
Refreshing Your WordPress Core Files
One of the oldest tricks in the hacker’s playbook is to hide malicious code inside the core WordPress files. These are the foundational building blocks of your site, which makes them an ideal hiding place.
Instead of trying to find a needle in a haystack, the safest and quickest fix is to simply replace them all with fresh, clean copies.
Here's how you do it:
- Get a Fresh Copy: Head over to the official WordPress.org release archive and download the exact same version of WordPress you are currently running.
- Unzip the Files: Unpack the downloaded zip file on your computer.
- Delete the Old Folders: Using your hosting file manager or an FTP client, delete the
wp-adminandwp-includesfolders from your server. Be very careful not to delete thewp-contentfolder or thewp-config.phpfile. - Upload the New Folders: Now, upload the brand new
wp-adminandwp-includesfolders you just unzipped. You'll also want to upload all the individual files from the root of the new WordPress folder, letting them overwrite the old ones on your server.
This one action alone often gets rid of a huge chunk of a typical infection.
Inspecting Themes and Plugins
Plugins and themes are, by far, the most common entry points for attacks. In fact, research shows that malware is responsible for around 72.7% of WordPress site infections, making it the number one hacking method. This fact alone should tell you why a thorough check here is non-negotiable.
Your best bet is to delete and reinstall your themes and plugins from the official repository or directly from the developer. This guarantees you’re getting clean, untampered code.
A Crucial Tip From Experience: If you use premium plugins or themes, download fresh copies directly from the developer's official website. Never, ever be tempted to use "nulled" or free versions from unofficial sites—they are almost always bundled with malware from the get-go.
Cleaning Up Key Configuration Files
Two files are absolute goldmines for hackers because they offer so much control over your site: .htaccess and wp-config.php. You need to inspect both of them very carefully.
- The
.htaccessFile: This file controls server rules, and hackers love to add malicious redirects here. The easiest way to clean it is to delete the current file and let WordPress generate a fresh, default one. Just go to Settings > Permalinks in your WordPress dashboard and click "Save Changes." That's it. - The
wp-config.phpFile: This is the heart of your WordPress installation, holding your database connection details. It’s a favourite hiding spot for malware. The best way to check it is to compare yourwp-config.phpwith thewp-config-sample.phpfile included in a fresh WordPress download. Look for any weird, long strings of code or suspicious functions and carefully delete them.
Hunting for Malware in Your Database
Finally, attackers often inject spam links or malicious scripts directly into your site’s database. A good security plugin like Wordfence or Sucuri can scan your database for these kinds of injections.
If the scanner finds anything, it will usually give you an option to remove the malicious content automatically. This is much safer than trying to edit the database by hand unless you really know what you're doing.
Tackling this entire process can be a lot to handle on your own. For a more detailed breakdown, you can check out our comprehensive guide on how to remove malware from WordPress.
Malware Removal Methods At a Glance
To make sense of the options, here’s a quick comparison of the common approaches to cleaning a WordPress site.
| Method | Best For | Pros | Cons |
|---|---|---|---|
| DIY Manual Cleaning | Users with technical confidence and a good understanding of WordPress file structure. | Free (costs time, not money); you learn a lot about your site. | Time-consuming; high risk of breaking the site if done incorrectly; you might miss something. |
| Security Plugins | Most WordPress users, from beginners to intermediates. Good for initial scans and automated cleanup. | Relatively easy to use; automated scanning and one-click fixes; affordable. | May not catch all malware types; premium features often required for full removal. |
| Professional Service | Business-critical websites, complex infections, or when you just want it handled by an expert. | Guaranteed removal; thorough and fast; peace of mind. | Can be expensive; requires trusting a third party with site access. |
The right method depends on your comfort level with the technical side of things and how critical it is to get your site back online quickly and safely.
If you’ve worked through these steps, give yourself a pat on the back. Successfully cleaning your site is a huge accomplishment. This process not only helps in removing malware from your WordPress installation but also gives you a much deeper understanding of how your site actually works.
How to Harden Your WordPress Security After a Cleanup

You’ve done the hard work of clearing out the infection. Take a moment to appreciate that—you’ve just performed the digital equivalent of major surgery on your website. But now is not the time to relax. Getting rid of malware is only half the battle; the next, absolutely crucial phase is making sure it can never get back in.
This is where we shift from reactive cleaning to proactive defence. We're going to build a stronger, more resilient fortress around your site. Think of it as changing the locks and installing a modern alarm system after a break-in. These steps are essential for preventing a repeat nightmare.
Your Immediate Security Lockdown
The very first thing you need to do is change every single password associated with your website. Once hackers have been inside your system, you have to assume they’ve grabbed every credential they could find.
Here's your immediate password reset checklist:
- All WordPress Admin Accounts: Every user with an administrator role needs a new, strong, unique password.
- FTP/SFTP Accounts: These provide direct access to your server files and are a prime target.
- Hosting Control Panel: Change the login for your cPanel, Plesk, or whatever dashboard your host provides.
- Database Password: This one is easy to overlook but critically important. You can usually update this through your hosting control panel, but remember to update your
wp-config.phpfile to match.
Don't just make them slightly different. Use a password manager to generate long, complex, and completely random passwords for each account. This single action slams the most obvious door shut.
Implementing Two-Factor Authentication
If passwords are your front door lock, Two-Factor Authentication (2FA) is the deadbolt. It requires a second piece of information to log in—usually a temporary code from an app on your phone. This means that even if a hacker somehow steals your password, they still can't get in.
Setting up 2FA on a WordPress site is incredibly straightforward. Plugins like Wordfence or other dedicated 2FA plugins can be configured in minutes. It’s one of the single most effective security measures you can take.
The reality is that WordPress sites face a relentless barrage of attacks. The WordPress threat landscape from recent statistics shows that a huge number of sites are vulnerable. Proactive security isn't just wise—it's essential for survival.
Setting Up a Web Application Firewall
A Web Application Firewall (WAF) acts as a protective shield between your website and the internet. It intelligently filters all incoming traffic, identifying and blocking malicious requests before they can ever reach your site to exploit a vulnerability. It’s like having a security guard at the entrance, turning away suspicious characters.
You generally have two choices when it comes to WAFs:
- Plugin-Based WAFs: These are integrated directly into WordPress via security plugins. They’re easy to set up and do a good job of blocking many common threats.
- Cloud-Based WAFs: These services (like Cloudflare or Sucuri) operate at the network level, meaning they block bad traffic before it even hits your server. This offers a higher level of protection.
Using a WAF drastically reduces your site's exposure to automated bot attacks. By layering these defences—strong passwords, 2FA, and a WAF—you transform your site from an easy target into a much tougher nut to crack. For more tips on creating a robust defence, check out our guide on website security best practices.
Taking these steps isn't just about cleaning up after an attack; it's about fundamentally upgrading your security for the long term. This process builds the resilience needed to keep your website safe and secure.
Knowing When to Call a Professional for Help
Tackling a WordPress malware infection on your own is a huge task, and sometimes, the DIY approach just doesn't cut it. And that's absolutely okay. Knowing when to call in an expert isn't admitting defeat—it's a smart, strategic move to protect your business and your own sanity.
Some situations really do call for a specialist. It all comes down to being honest about your own skills and the severity of the infection you're up against.
Red Flags That Signal You Need an Expert
Have you been stuck in that frustrating loop? You spend hours cleaning your site, only to see the same infection pop up a few days later. This is a classic sign that the malware is buried deeper than you can see. Hackers are notorious for leaving hidden backdoors that are incredibly tricky for a non-expert to find.
It’s probably time to call a professional if any of this sounds familiar:
- Recurring Infections: You clean everything up, but the malware keeps coming back. This almost always points to a hidden backdoor that standard tools can't find.
- You're Overwhelmed or Short on Time: A proper malware cleanup is a painstaking, time-intensive job. If you're running a business, your time is far better spent doing what you do best.
- The Hack is Too Complex: Are you seeing bizarre server errors? Has the malware broken core parts of your site? These are signs of a sophisticated attack that needs a specialist's touch.
- Your Site Has Been Blacklisted: If Google has flagged your site with that dreaded red warning screen, getting off the blacklist can be a bureaucratic process. Professionals navigate these review requests every day and know exactly what to do.
Handing a complex malware problem over to a pro isn't just about cleaning the site. It’s about buying back your peace of mind and getting a guarantee that the job is done right the first time.
The Value of a Professional Service
Bringing in an expert service gives you more than just technical help; it provides a clear, guaranteed path to getting your site back when you feel completely stuck. Reputable services will stand by their work, offering guaranteed malware removal—meaning they won't stop until your site is 100% clean.
They also come equipped with specialised tools that can spot and destroy threats that most security plugins might miss entirely. This comprehensive approach means they don't just fix the immediate problem; they also find and patch the vulnerabilities that let the attackers in.
If you feel like you've hit a brick wall, exploring professional WordPress malware removal services is the most sensible next step. The goal is to get your website healthy and secure again. If you're feeling out of your depth, don't hesitate to get an expert on your side.
Common Questions About WordPress Malware
Once the dust has settled and you’ve managed to get your site back online, it’s completely normal to have some questions buzzing around. The immediate crisis might be over, but that feeling of uncertainty can stick around. Let’s clear the air and tackle some of the most common things people ask after they’ve dealt with a WordPress hack.
Think of this as a quick chat to put your mind at ease. We'll go through the practical questions that almost always come up after you've done the hard work of removing malware from your WordPress site.
How Did My Site Get Malware in the First Place?
This is usually the very first question on everyone's mind, and the answer is almost never personal. It’s highly unlikely that a hacker specifically targeted you or your business. More often than not, it’s an automated bot that was just scanning the web for an easy way in.
So, where do they get in? Here are the usual suspects:
- Outdated Plugins or Themes: This is the big one. Honestly, it’s the cause 90% of the time. A single plugin left un-updated can have a known vulnerability that bots are programmed to find and exploit.
- Weak Passwords: Simple passwords like "Password123" or using the same one for multiple accounts is like leaving your front door wide open.
- Dodgy Hosting: While less of an issue with good quality hosts, some shared hosting setups can have security weaknesses that create a domino effect, impacting every site on that server.
Knowing how they got in is the key to making sure it never happens again.
Will This Malware Incident Hurt My Site's SEO?
That’s a perfectly valid worry. Here's the good news: cleaning the malware is what saves your SEO. It's the active infection that does the real damage.
When Google finds malware, it often blacklists your site. This means visitors see a big, scary warning screen, and your search rankings will plummet. The moment you clean the site, you can head over to Google Search Console and request a review. This tells Google, "Hey, we're safe now!" and they'll lift the penalty. Your rankings will then start to recover.
The key takeaway is this: A swift and thorough cleanup is the best thing you can do for your SEO post-hack. Leaving the malware in place is what causes long-term damage.
Why Can’t I Just Restore an Old Backup?
On the surface, restoring a backup seems like the perfect quick fix. But it's a gamble that usually doesn't pay off. The main problem is you simply don't know when the site was infected. Malware can lie dormant for weeks, or even months, meaning your backup could already be compromised.
And even if you get lucky and restore a clean version, the security hole that let the hackers in—like that out-of-date plugin—is almost certainly still there. All you've done is reset the clock until the next bot comes along and finds the exact same vulnerability.
What Does Professional Malware Removal Cost in the UK?
If you decide that doing it yourself is just too much hassle, you’ll want to know what to expect in terms of cost. Here in the UK, most professional WordPress malware removal services will offer a one-time fix. The price can vary a fair bit, depending on how deep the infection goes.
Many specialists also provide ongoing monthly security plans. This is a much better long-term strategy. Instead of waiting for a disaster, these plans proactively protect your site with firewalls, constant monitoring, and regular updates to stop infections before they start. It's about prevention, not just cure.
If you're still feeling stuck or just want the peace of mind that comes with professional help, LINX Repair Websites is here for you. We offer guaranteed malware removal and ongoing care to keep your site secure. Contact us to learn more.
